|
|
I've been getting dismayed customers here for more years than I care to remember. Often it's a PC and frequently a laptop. The other day a neighbour called to say he thought he'd fallen victim to an email scam and was unable to use his computer properly. Whenever he attempted to do certain things, such as responding to a message that his trial period for a particular anti-virus package had expired a message popped up requesting an Administrator password or "No", with the "Yes" box greyed out. If he'd actually known the Administrator password he couldn't have proceeded because there wasn't a box into which this could be typed. Basically,what had happened was that his account had been stripped of Administrator Rights and many things one takes for granted were now impossible. For example things such as "MSCONFIG", "SYSTEM RESTORE", and of course access to the Control Panel section on "USER ACCOUNTS". A skim through the Internet revealed what has been getting worse over the years... masses of useless information; however.. mixed up in this were some clues which eventually enabled me to fix the problem and here I'm going to explain how to do this. |
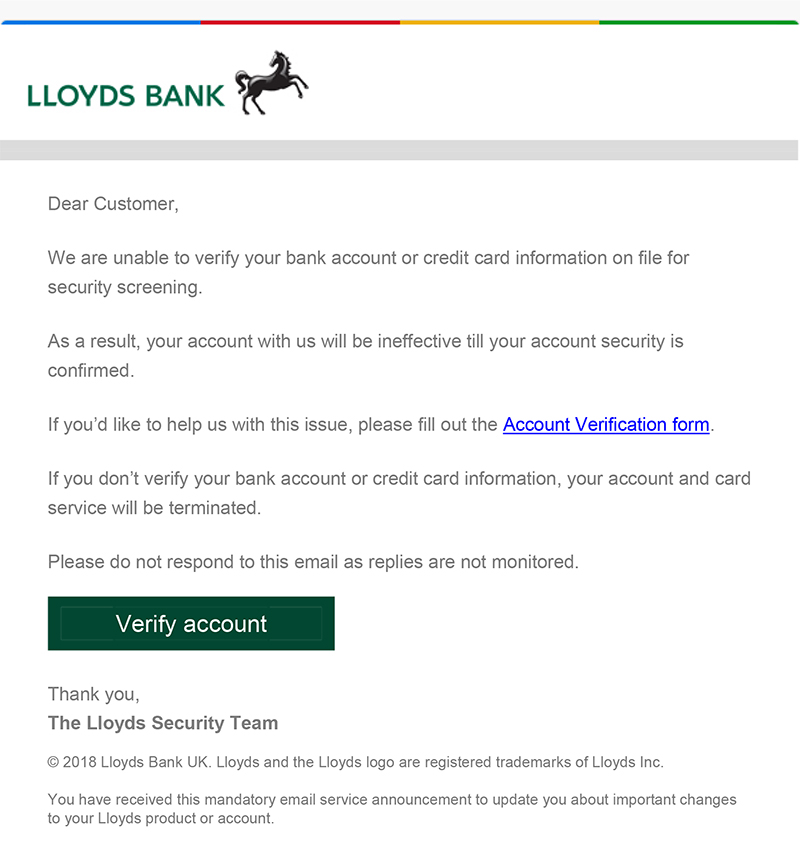
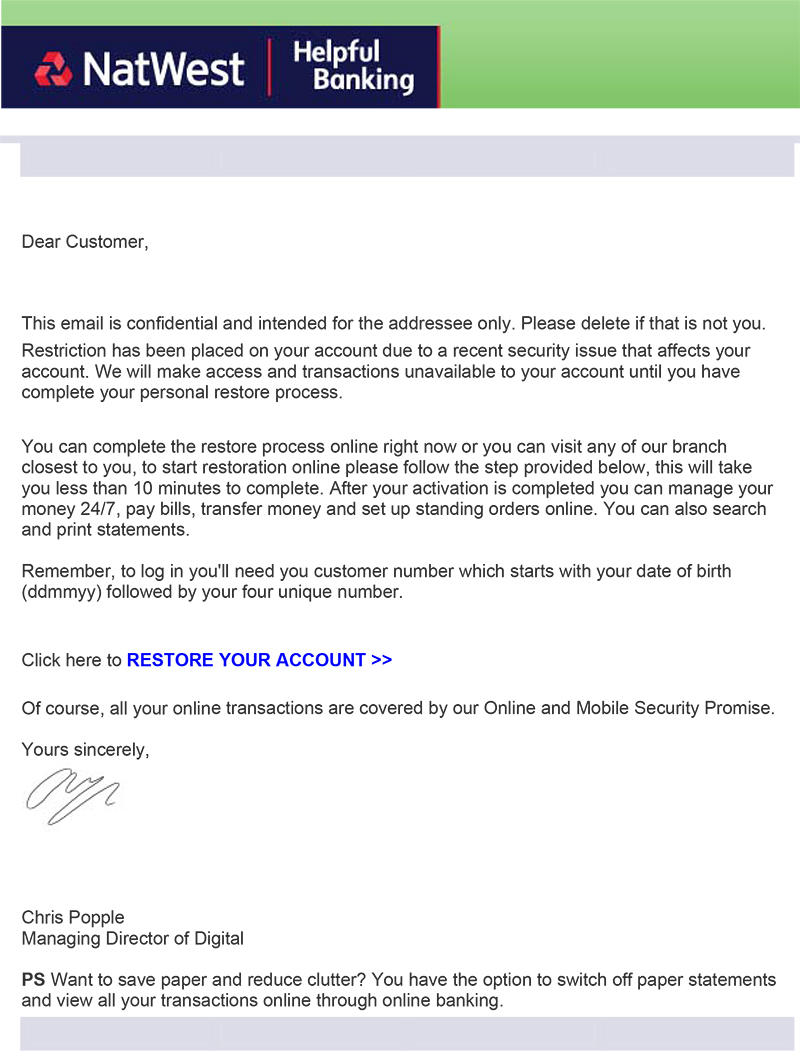
| First, I'll briefly explain how the problem occurred. Mixed up in most emails that one receives are rogues which are designed to fool a user into parting with vital information which would enable someone to do nasty things such as pinch your hard earned cash. I get at least one or two of these emails every day and as time has passed these emails have got more and more clever. When my monthly BT statement arrives I get not one, but two messages. One is OK but the other attempts to steal my account details including the password. It's not always easy to spot a rogue because the embedded links are often OK and point to the real website and, in cases where an official website has been hacked, you're directed to a page within the website that's not genuine (ie.the hacker has embedded his own set of pages within the official website). Here's the rogue not from BT... |
 |
|
|
 |
 |
|
What about lost Administrator Rights? Sometimes a rogue email will cause, some way or other, the execution of code which renders your computer unable to carry out certain functions. For example, if the code has placed a virus in your PC which is able to steal information then it would be nice if the virus can be free to do its dirty work unopposed. True, if you have an anti-virus program, this may help, but often this program may be a trifle late in detecting a problem, and it's only very rarely such a program can reverse the bad effects. So, this is the problem I'm facing today. The laptop seems to be safe from the attempted hijack, but is suffering from the initial attack viz. the main user has lost Administrative Rights and is effectively locked out of his own computer for all but basic applications. Of course the method of restoring full use of the computer is complicated because, if it was easy, then a would-be hacker would be free to do anything he wishes. For example, delete, or change your Desktop password. To get around the loss of Administrator Rights then, requires some subterfuge. This is the way it's done. |
|
When you're turning on a computer that has a password into the Desktop you'll see a screen where you need to type your password. At this point a user hasn't gained access to the computer so ostensibly a hacker has certain unrestricted rights, but how does one take advantage of this? Well, if only we could just type in commands.. but we can't because we need to type a password to open the Desktop and then open Command Prompt. In fact, if you did type the password and attempt to open Command Prompt as Administrator you'd get nowhere because you'd be asked to type an Administrator password but nowhere to type it... which is where we started. There's a backdoor into Windows 7 and with some fiddling we can use it. Windows designers needed to deal with a potential problem that could affect normal users and that is when say a book has inadvertently slid over the end of your keyboard. If the book was to rest on a key this would mess up typing a password so the designers came up with a piece of code that detects a few keyboard mishaps which is known as "Sticky Keys" which can also be used to advantage by some disabled people who can't combine key presses. The code is named "sethc.exe" and needs to run with Administrator Rights. What we need to do is to run sethc.exe but not to sort out sticky key problems, but instead to open Command Prompt as Administrator. Anyone with basic programming knowledge can see how this can be done... Access the hard drive.. open the Windows folder.. open System32... find sethc.exe and rename this to say sethc.exx.. then copy cmd.exe as sethc.exe. This sounds easy but you need to have some technical knowledge and I'm assuming you have this. If not then contact someone that does and show them this advice. |
|
Having placed Command Prompt's foot into Windows back door, boot the computer and wait until the password box appears. Tap the Shift key say 5 times and instead of the Sticky Key response you'll see the reassuring Command Prompt window. Now we have to figure out how to provide Administrator Rights to the main computer user. There are several ways but the best is to create a new user with Administrative Rights then log onto this new account and simply give Administrative Rights to the main computer user. Remember that these rights had been removed by our virus writer and all we're doing is making good the mess. Creating a new user is straightforward, and I've used the same details as the chap from whom I got the tip (that worked)... net user /add v4L 12345 net localgroup administrators v4L /add What we've done is create a new user called v4L with a password 12345 Now reboot, log onto v4L using the password 12345 and change the Account details for the main user by ticking their Administrative Rights box. This fixes the problem created by the virus and you can then tidy up by removing the dummy user and putting back the Sticky Keys program etc... The above method is also useful if you get a customer who has forgotten their Desktop password, but let's leave that for now. |
|
I was happy that the fault had cleared up but surprised when the laptop owner returned with a second problem. He was unable to open links in Outlook 2003. No trouble I said after looking for a Microsoft explanation and finding an easy solution.. just run a little program and all will be well. Hang on, I said, I'll fix this in a jiffy. Of course it wasn't an easy fix after all. The simple Microsoft fix commenced with a System Restore point being generated and after a few minutes you could see this wasn't going to happen. My customer then chimed up... System Restore has never worked... Leave it with me I said and eventually found the lack of email link problem was a bug. Was it a bug in Windows 7, Outlook, or Internet Explorer? It was in fact a problem associated with Firefox. Buried in the Registry are some keys linking HTML files with their method of opening. The HTML file type was renamed Firefox HTML. I opened Registry Editor and set HTML and a couple of similar file types back to plain HTML... checked Outlook and the links worked fine. Now to look at the System Restore problem. Microsoft Windows 7 was convinced it was a hard disk error caused by a corrupted block or two, but I don't believe the diagnosis. I suspect the problem is due to multiple anti-virus programs hanging around the Registry. Fragments of obsolete programs are clashing and somehow preventing certain types of hard disk writes. Because I'm not sure which of the several anti-virus programs have been paid for I drew the line at sorting this out included with the other faults. The laptop has a Microsoft anti-virus, two versions of McAfee and a version of Vipre... and maybe more? Maybe on another day I might tackle this... |